CredSSP Encryption Oracle Remediation
Overview
There is a solution to a CredSSP vulnerability, the “Remote Code Execution” (CVE-2018-0886). However, it may affect RDP linkages. The linkage was released in the March 2018 Security Newsletter. The exploits that we observed were vulnerable:
- Targets receive a malicious RTF Microsoft Office document.
- After opening, the malicious document allows the exploit’s second phase to be downloaded as a malicious code HTML page.
- The malicious code triggers the use-after-free memory-corruption bug
Accompanying shellcode. Then, it downloads and executes a malicious payload.
Symptoms
1. The VM screenshot shows the OS fully loaded and waiting for the credentials
2. If you try to RDP the VM either internally or externally, you’ll get the message:
“An authentication error has occurred.”
“This could be due to CredSSP encryption oracle remediation.”
For more information, see Microsoft Support.
Root Cause Analysis
In May, a monthly Windows update resolved a vulnerability issue in the Credential Security Support Provider (CredSSP) protocol. It contains two things:
- Correct how Credential Security Support Provider protocol (CredSSP) validates requests during the authentication process
- Change the group policy Encryption Oracle Remediation default setting from Vulnerable to Mitigated.
If the server or client has distinct expectations when setting up a secure RDP session, it could block the connection.
Moreover, there is the possibility that the current default setting could change from the tentative update. Therefore, it impacts the secure session requirement.
Below is the matrix for each possible situation for RDP result:

Examples:
If both client & server come with a default setting (Mitigated), RDP will work in a secure way.
Resolution/ Fix
Be sure to install the recent patch on both client and server sides, so RDP is set up safely.
Alternative Workarounds
Mitigation 1
In other words, we could consider changing the policy settings of the customer to temporarily acquire RDP access to the servers if you cannot RDP to your patched client to VM.
Then, you can change the settings in the Local Group Policy Editor. Next, Execute gpedit.msc and browse to Computer Configuration / Administrative Templates / System / Credentials Delegation in the left panel:
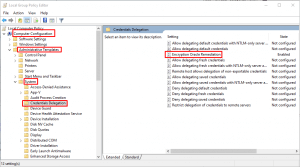
In other words, we could consider changing the policy settings of the customer to temporarily acquire RDP access to the servers if you cannot RDP to your patched client to VM.
Then, you can change the settings in the Local Group Policy Editor. Next, Execute gpedit.msc and browse to Computer Configuration / Administrative Templates / System / Credentials Delegation in the left panel:




